Using the solution
Automatic deployment options
There are two different automatic deployment options:
- Using Config Sync
- Using Eventarc, Cloud Workflow and Cloud Deploy
Updating Deployed Application Containers using Anthos Config Sync
Config Sync is an open source tool that lets cluster operators and platform administrators deploy consistent configurations and policies. This step is not mandatory, but setup Anthos Config Sync allows Anthos to monitor applications running on the edge server and apply required policies to the edge server.
This is also an automatic way to deploy new application images to edge services, Anthos will periodically check if the application is running and try to bring it up if it’s not.
Prerequisites
- You must already have a Kubernetes cluster attached to Anthos, or have an Anthos Bare Metal cluster configured.
- Enable Anthos Config-Sync feature. If you provisioned the Cloud Resources via Terraform, this feature is enabled already.
- Create a Service Account and a Source Repository, and grant the service account required access. If you provisioned the Cloud Resources via Terraform, this service account and Source Repository is created and configured already.
Configure Anthos Config Sync
Run on Setup Workstation
-
Grant
viai-acm-repo-readerservice account the roleiam.workloadIdentiyUSerexport DEFAULT_PROJECT=$PROJECT_ID export SOURCE_REPO_NAME=acm-repo export SVC_ACCOUNT=viai-acm-repo-reader@${DEFAULT_PROJECT}.iam.gserviceaccount.com gcloud config set project $DEFAULT_PROJECT gcloud iam service-accounts add-iam-policy-binding \ --role roles/iam.workloadIdentityUser \ --member "serviceAccount:${DEFAULT_PROJECT}.svc.id.goog[config-management-system/root-reconciler]" \ ${SVC_ACCOUNT}Where:
DEFAULT_PROJECTis the GCP project IDSOURCE_REPO_NAMEis the Source Repository name, defaults toacm-repoSVC_ACCOUNTis the service account, defaults toviai-acm-repo-reader@${PROJECT_ID}.iam.gserviceaccount.com
-
Push the Kubernetes manifest files to the Source Repository.
export SOURCE_CODE_FOLDER_PATH=${OUTPUT_FOLDER}/kubernetes export GOOGLE_CLOUD_DEFAULT_USER_EMAIL="<YOUR GOOGLE CLOUD USER ACCOUNT>" export WORKING_DIR=$(pwd) cd ${OUTPUT_FOLDER} gcloud source repos clone acm-repo --project=kalschi-viai-20221207-005 cp -r ${OUTPUT_FOLDER}/kubernetes/* ${OUTPUT_FOLDER}/acm-repo cd ${OUTPUT_FOLDER}/acm-repo/ git add . git commit -m "update" git push cd ${WORKING_DIR}Where:
SOURCE_CODE_FOLDER_PATHcontains the kubernetes manifest files generated by previous stepsGOOGLE_CLOUD_DEFAULT_USER_EMAILthe user email of Anthos administrator. This user will be assigned required roles to configure the Anthos.OUTPUT_FOLDERthe folder which contains Visual Inspection AI Edge application yaml files.
-
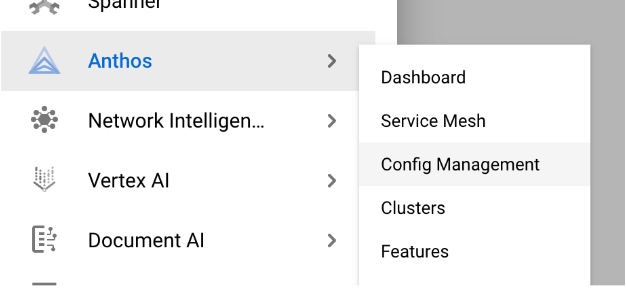
In the Google Cloud console, navigate to ‘Anthos’ -> ‘Config Management’
-
Create a New Setup
-
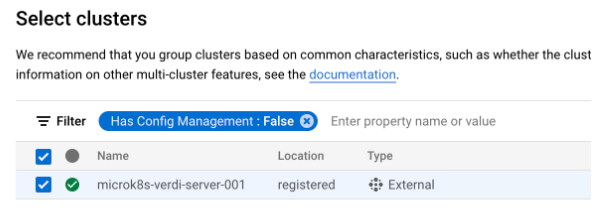
Select your cluster to set up Config Sync, then click Next
-
Skip the policy controller setup page
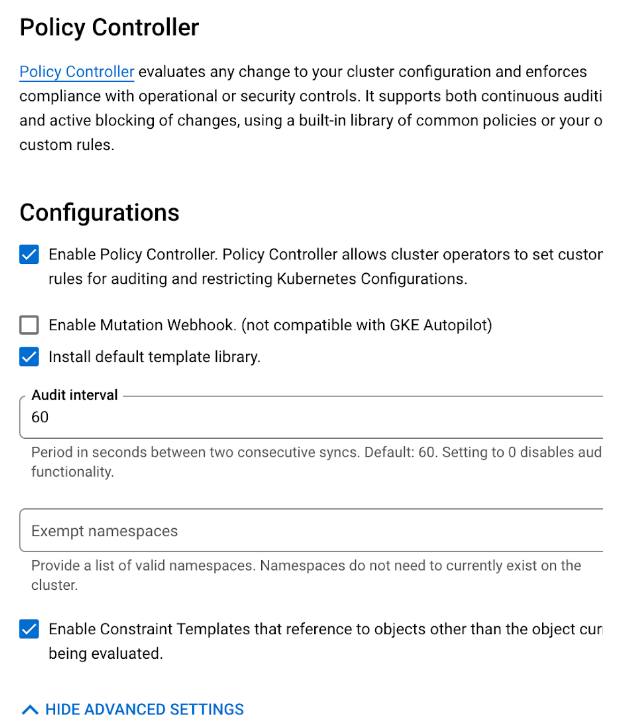
-
In the next screen, select Custom repository
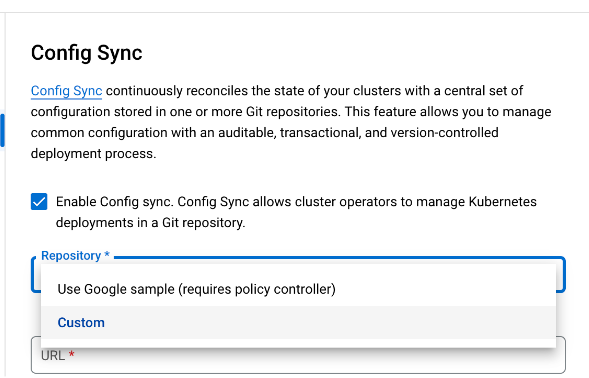
-
Expand the ‘Advanced’ section, type in the repository URL.
It should be in this format:
https://source.developers.google.com/p/<PROJECT_ID>/r/acm-repo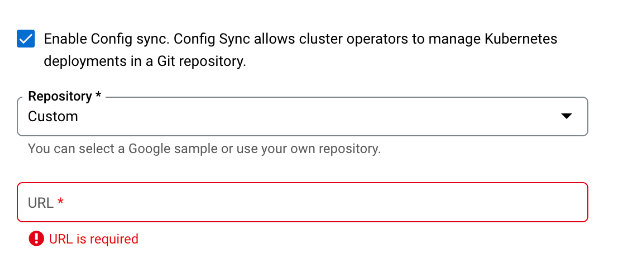
-
Select
Workload Identityin the ‘Authentication type’ dropdown and add the service account you previously created as ‘GCP Service Account Email’The service account should be similar to
viai-acm-repo-reader@<PROJECT_ID>.iam.gserviceaccount.com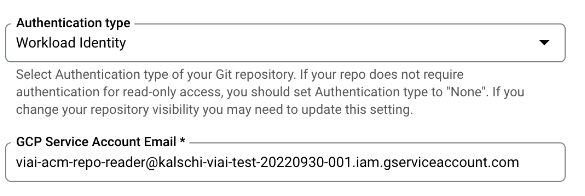
-
Leave the rest of the fields with the default values and click ‘Complete’
-
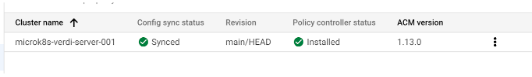
After a few minutes you should see Config Sync statys ‘Synced’
Automatic deployment with Eventarc, Cloud Workflow and Cloud Deploy
This deployment pipeline provides default service templates for the most common use cases. You can update the template files to fit your needs.
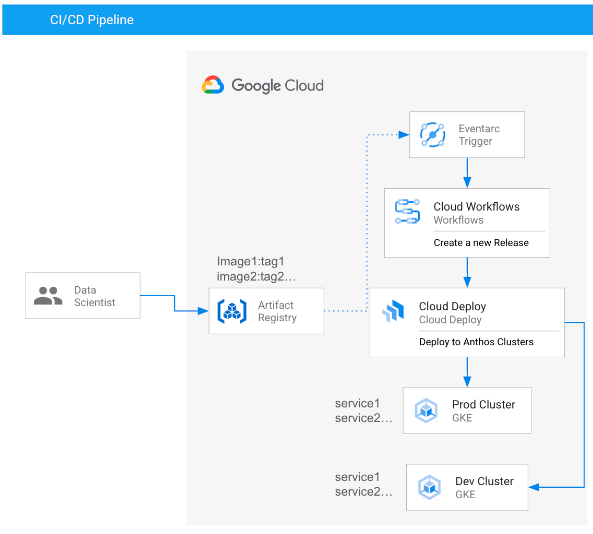
This deployment pipeline does the following:
- Monitor if a new container image is pushed to the Artifacts Registry.
- Eventarc Trigger triggers a workflow when new images are pushed.
- The workflow triggers the Cloud Deploy delivery pipeline.
- The delivery pipeline downloads Skaffold and Kubernetes manifest files from Storage Bucket, renders results and creates a Cloud Deploy Release.
- The service name is set to the image name by default. You can change this by customizing the pipeline.
Customize the Kubernetes manifests
You can customize the deployment and service by modifying the Skaffold and Kubernetes YAML files.
- Default template files
- Kubernetes service template files are in
kubernetes/viai-model/viai-model.tmpl - Skaffold template files are in
kubernetes/viai-model/skaffold.tmpl
- Kubernetes service template files are in
- Update
kubernetes/viai-model/viai-model.yaml, replace${SERVICE_NAME}with the container image name.
For example, if the Visual Inspection AI trained model container image is stored at gcr.io/my-project/my-viai-model:version-001. The SERVICE_NAME should be my-viai-model
Run on Setup Workstation
-
Update Skaffold and Kubernetes manifest files, compress as .tat.gz file and upload to Cloud Storage Bucket
cd ${OUTPUT_FOLDER}/kubernetes/viai-model tar -czf "${OUTPUT_FOLDER}"/"${SERVICE_NAME}".tar.gz \ -C "${OUTPUT_FOLDER}" viai-model.yaml skaffold.yaml gsutil cp "${OUTPUT_FOLDER}"/"${SERVICE_NAME}".tar.gz gs://${DEFAULT_PROJECT}_cloudbuild/viai-models/${SERVICE_NAME}.tar.gzWhere:
OUTPUT_FOLDERThe folder which containsskaffold.yamlandviai-model.yamlSERVICE_NAMEThe name of the service which will be created in the target edge server, this value should equals to container image name, For example, if the Visual Inspection AI trained model container image is store atgcr.io/my-project/my-viai-model:version-001. The SERVICE_NAME should bemy-viai-model
Customize the Workflow
The deployment pipeline creates a Cloud Workflow to invoke and kick-off a Cloud Deploy delivery pipeline.
Run on Setup Workstation
The Cloud Workflow definition is in terraform/model-deployment-pipeline/main.tf
resource "google_workflows_workflow" "event-trigger-destination" {
for_each = toset(var.image_name)
name = "workflow-${each.key}-${var.anthos_target_cluster_membership}"
project = var.google_viai_project_id
region = var.google_default_region
source_contents = <<-EOF
…<WORKFLOW DEFINITION>
EOF
The Cloud Deploy Deliver pipeline definition is defined in terraform/model-deployment-pipeline/main.tf
resource "google_clouddeploy_target" "dev" {
for_each = toset(var.image_name)
location = var.google_default_region
name = "${each.key}-${var.anthos_target_cluster_membership}"
project = var.google_viai_project_id
anthos_cluster {
membership = "projects/${var.google_viai_project_id}/locations/global/memberships/${var.anthos_target_cluster_membership}"
}
require_approval = false
execution_configs {
usages = [ "RENDER", "DEPLOY" ]
service_account = "viai-abm-service@${var.google_viai_project_id}.iam.gserviceaccount.com"
}
}
Update the deployment pipeline
Run on Setup Workstation
When you provision the Google Cloud resources, add -e ${ANTHOS-MEMBERSHIP-NAME} and execute the provision-terraform.sh script.
A default deployment pipeline that deploys applications to the Anthos cluster specified is automatically created for you. You can update the pipeline to fit your business needs.
For example:
export MEMBERSHIP=<YOUR ANTHOS MEMBERSHIP NAME>
scripts/provisioning-terraform.sh \
-a \
-g \
-l "${VIAI_STORAGE_BUCKET_LOCATION}" \
-p "${DEFAULT_PROJECT}" \
-r "${DEFAULT_REGION}" \
-z "${DEFAULT_ZONE}" \
-m "${GOOGLE_CLOUD_DEFAULT_USER_EMAIL}" \
—c "${VIAI_CAMERA_INTEGRATION_SOURCE_REPO_URL}" \
—b "${VIAI_CAMERA_INTEGRATION_SOURCE_REPO_BRANCH}" \
-e "${MEMBERSHIP}" \
-x
To update the deployment pipeline. Update the google_workflows_workflow resource defined in ${VIAI_PROVISION_FOLDER}/terraform/model-deployment-pipeline/main.tf And re-run the provision script again.
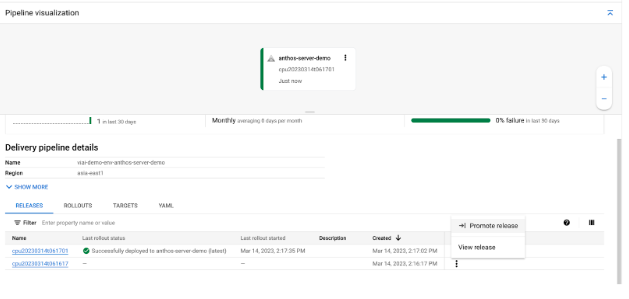
Promote Model Release
When new models are trained and published to the Artifact Registry. The EventArc triggers Cloud Workflow and deploys the new model to the edge server.
Go to Cloud Deploy console, you should see a new release been created, to deploy the model to the edge server, you just need to promote the release.